SafeBook
(Redirected from Safebook (Cutillo et al., 2011))
Jump to navigation
Jump to search
A SafeBook is a Decentralized Peer-to-Peer (P2P) Network in which each user's data is partitioned, replicated, encrypted and stored at the nodes of trusted peers.
- Context:
- It was first developed by Cutillo et al. (2011).
- It can include the following DOSN's services:
- data management by the user (partial);
- 24/7 data availability (partial);
- data transfer;
- data encryption;
- data loading and processing delay;
- social network relationship management (partial).
- Example(s):
- …
- Counter-Example(s):
- See: Centralized Online Social Network, Centralized Computing System, Decentralized Application (DApp), Decentralized Cloud System, Decentralized Clinical Trial, Decentralized Research, Decentralized Digital Currency.
References
2017
- (Muller et al., 2017) ⇒ Andre Muller, Andre Ludwig, and Bogdan Franczyk (2017). "Data Security In Decentralized Cloud Systems – System Comparison, Requirements Analysis And Organizational Levels". In: SpringerOpen - Journal of Cloud Computing.
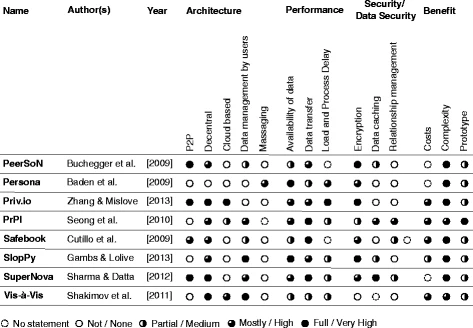
- QUOTE: The results of the comparison are summarized in Fig. 1. The solutions of the investigated concepts of PeerSoN (Buchegger et al., 2009), Priv.io (Zhang and Mislove, 2013), Safebook (Cutillo et al., 2011), and SuperNova (Sharma & Datta, 2012) are based on a peer-to-peer approach. The concepts PrPl (Seong et al., 2010), SlopPy (Gambs & Lolive, 2012), and Vis-à-Vis (Shakimov et al., 2011) are based on distributed applications and on server solutions as well as cloud solutions that are self-managed by the user. As a common ground of these concepts, all parties are expected to run and manage their own cloud system. The eight already mentioned systems will now be explained shortly and examined with regard to their currently unsolved problems.
|
2011
- (Cutillo et al., 2011) ⇒ Leucio Antonio Cutillo, Refik Molva and Melek Onen (2011, June). “Safebook: A distributed privacy preserving Online Social Network". In: Proceedings of the 12th IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks (WOWMOM 2011).
- QUOTE: In Safebook each user's data is partitioned and replicated and the encrypted replicas of a user's data are stored at the nodes of that user's trusted friends. The untraceability of the communications during look-up and data retrieval operations is assured thanks to an additional feature of Safebook in that the messages between a requester node and a friend's node that serves the request always route through several hops in order to hide a user's social links that are reflected by the OSN graph. Safebook defines two identities for each peer, namely the node and user identifiers, to prevent the disclosure of sensitive friendship information originating from an analysis on the data flows. Moreover, Safebook also prevents Sybil attacks thanks to the presence of a Trusted Identification Service which is contacted only once during the user registration phase in order to generate a unique and unforgeable identifier per user. The introduction of this third party does not impact the decentralized nature of Safebook's architecture since it is not involved in any data communication or data management operation.